| University | Yoobee College of Creative Innovation |
| Subject | CIT504 Introduction to Information Technology |
CIT504 Assessment 2
Programme: NZ Certificate in Information Technology (NZ2595, Version 2, Level 5, 60 Credits)
Course: CIT504: Introduction to Information Technology (15 Credits)
Assessment 2 : Case Study
Weighting within the course: 40%
Objective
Provide learners with basic IT concepts and an introduction to terminology. Helps understand the role of an IT professional in supporting organisational activities and requirements.
Learning Outcomes (LOs) covered
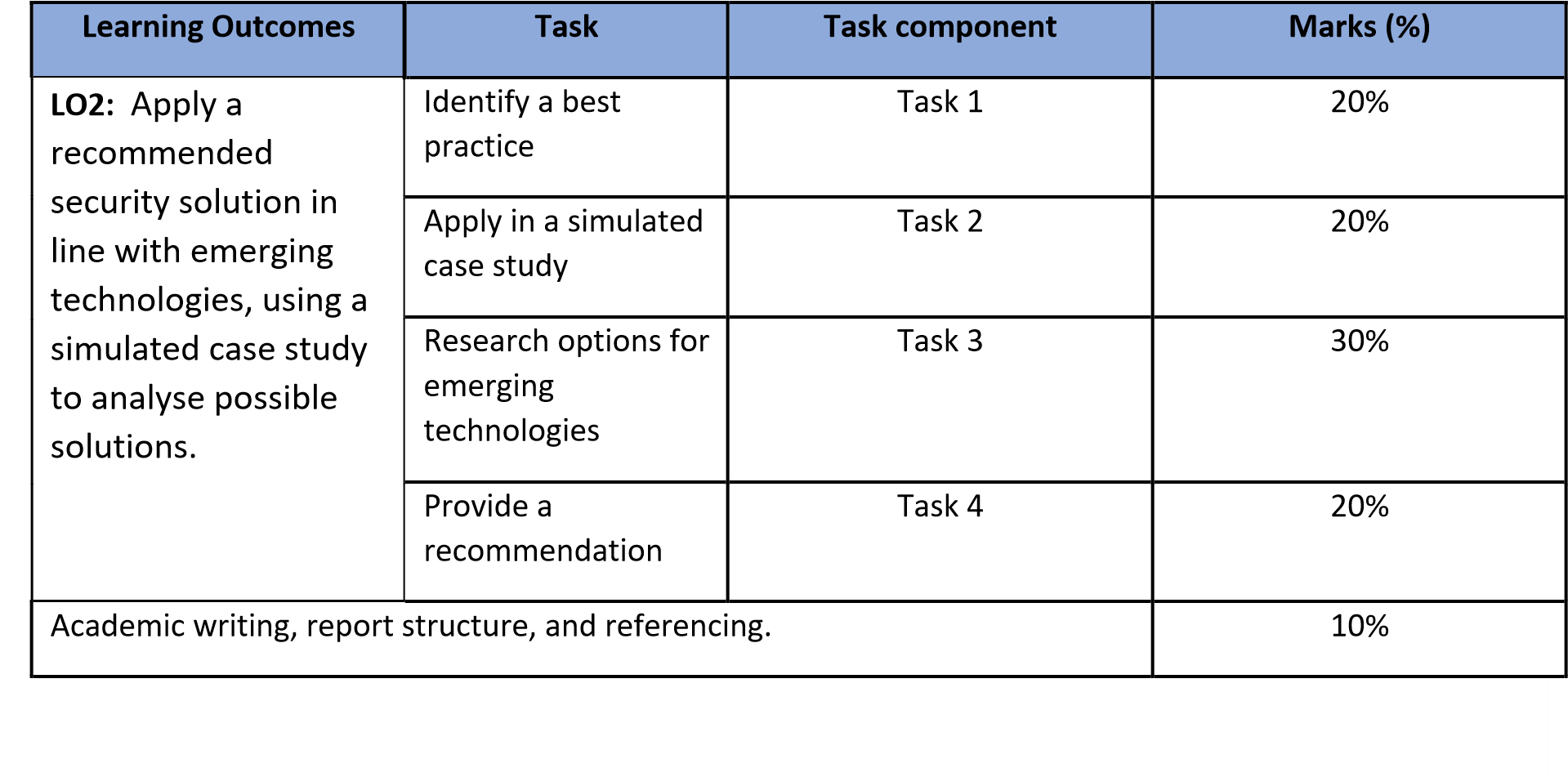
LO2: Apply a recommended security solution in line with emerging technologies, using a simulated case study to analyse possible solutions.
Qualification Graduate Profile Outcomes (GPOs) covered
GPO 1: Apply the fundamentals of IT technical support concepts and practice to securely manage hardware, software, and networking resources to support end users and meet security, ethical and organisational requirements. (LO2)
GPO 7: Apply communication, collaboration, teamwork, documentation and customer service skills to enhance effectiveness in an IT role.
Assessment Matrix
 Assessment Conditions
Assessment Conditions
- This is an open book assessment. To complete this assessment, utilise the course content, your personal notes, and external resources such as textbooks, online journals, or reliable sources.
- If you are unsure about what is required, ask your tutor.
- All work must be your own, any content from other sources must be cited and referenced.
- No limit on the time you can spend on assessment. However, it must be submitted by the due date.
- Research is required in this assessment. It is expected that you will be referring to information obtained from other sources. These sources must be identified by in text citations and references using APA 7. It is recommended that you use reference generators such as the one built into Microsoft Word.
- The purpose of this assessment is to assess your knowledge. In the event Yoobee suspects collusion or other lack of Academic Integrity, this will be addressed. For more information, please refer to the Student Handbook.
- Submit your completed assessment as a Word or PDF document online in the correct space provided. Some students are eligible for a change in the assessment conditions due to learning differences. If you consider this applicable applies to you, discuss it with your tutor before starting the assessment.
- Submissions can be made in English or Te Reo. Should you desire to submit in Te Reo, please make arrangements with your tutor.
Success Criteria
You need to receive 50% or more of the total marks available to pass this assessment. You must pass all assessments in the programme to be able to attain the Certificate in Information Technology.
Should you achieve 40 to 49% of the total marks available on the first submission of an assessment, you will have an opportunity to resubmit. This means that if you achieve at least 40% on the first submission you will have one additional opportunity to achieve 50%. Where a second submission is required, the marks available will be capped at 50%.
In addition to achieving a minimum of 50% in each assessment, ākonga must demonstrate achievement of all learning outcomes being assessed.
Grading
The final grade for the assessment will be determined by the score achieved based on the following table. Ākonga | learners are permitted one attempt per assessment task.
| Grade | Mark Band Range | Pass/Fail |
| A | Meet all requirements, mark range (80+) | Pass |
| B | Meet all requirements, mark range (65-79) | Pass |
| C | Meet all requirements, mark range (50-64) | Pass |
| D | Did not meet all requirements, mark range (4049) | Fail |
| E | Did not meet requirements – mark range (0-39) | Fail |
If a learner does not achieve a passing grade on the first attempt, they may be provided with one opportunity to re-sit per assessment. To be eligible to re-sit, a grade between 40 – 49% on the first attempt is required. 50% is the maximum grade awarded for a re-sit.
Please note
Failure to achieve a passing result after the re-sit may result in non-completion of the course and you may need to re-enrol in the course to progress in the programme of study.
A grade for the course will be calculated based on the weighting for each assessment in the course. To meet the requirements of this course, ākonga must achieve a minimum grade of 50% for all assessments. The final grade for the course will be determined by the score achieved in this assessment, plus Assessment 1 for this course.
Submission Requirements
The format of the report makes up 10% of the marks in the assessment. The required details are
- To be submitted as a Word or PDF document that contains your answers to all tasks below. This is to be submitted in the assessment section of Yoobee Online (the LMS) by the due date.
- The submission must have your name and student ID number on the Title Page, together with the Assessment number and title and due date.
- All answers must be labelled with a heading indicating task and subtask number and description, for example ο Task 1: ….
♣ Task1-1
♣ Task1-1
♣ Task1-2
♣ Task1-2
- Explanations should be in the format of “SEE”.
ο Statement about the topic
ο Explanation of why the statement is valid (with references if using a theory) ο Example relevant to the scenario
- Submission should be using 14 pt calibre, line spacing 1.5, and adhere to APA 7 if external sources are referenced. Use of reference generators is encouraged.
- There should be no more than 1,500 words, but the expected word count is about 1,000 words.
Assessment 2
Learning Objective: Apply a recommended security solution in line with emerging technologies, using a simulated case study to analyse possible solutions.
GPO covered: Apply the fundamentals of IT technical support concepts and practice to securely manage hardware, software, and networking resources to support end users and meet security, ethical and organisational requirements.
Requirements
The requirements of the task are that you should:
- Review the client scenario and identify and explain the security solution requirements
- Apply the solution in a simulated environment
- Research security options, including emerging technologies, and evaluate how well they meet the needs of the client.
- Provide a recommendation for an applied solution.
- Write a report to the IT manager with the recommendations and why they are appropriate. The report must be in the described format, with each statement justified with an explanation and an example of the significance.
Scenario
Client
ABC Print Services is a publishing company located in Hamilton that prepares material ready for printing in te reo Māori and English. A lot of the work is done in te reo Māori.
The Hamilton office has a printing press that can handle material up to A3 or a small A5 24 page booklet. There is also a sales team of five people and a publication team of three. There is also a financial manager and a general manager.
ABC Print Services is looking to set up a new sales office in Taupō to cover the South Waikato from
Putaruru to Tūrangi and as far west as Te Awamutu. Rotorua would have the choice of going to Taupō or Hamilton. The team will consist of three people, with each member spending three days a week on the road and two days in the office. There is also a sales support person who will be located in the office to help the sales people with a variety of tasks.
The Hamilton office has a Windows Domain Controller and a file server. The new office is to have a site-to-site VPN, a domain controller, and a workstation for the sales support person.
The server in Taupō is to:
- Authenticate users from the local office and from the head office when visiting
- Provide IP addresses to client devices
- Resolve hostname to IP address requests and locate key services
- Store files created by the staff so they can be backed up to the file server device in Hamilton
The sales support person will use their workstation to:
- Upload clients’ work to the network share for clients’ work on the file server
- Correspond with clients and suppliers using e-mail in te reo Māori and English
- Using templates, complete sales contracts for sales staff in te reo Māori and te reo Pakeha.
ABC Print Services use a number of Software as a Service (SaaS) providers including Microsoft 365 for email, Microsoft Teams, OneDrive as well as Office productivity applications. ABC Print Services also use cloud storage systems that use the Windows Domain Authentication system for access.
Your role
You have been requested to configure authentication according to best practices and recommend a solution that will help reduce the risk of unauthorised activity through user passwords being hacked.
Task 1: Identify the client’s security requirements (20%)
Authentication is a major part of data security systems. With Windows Domain authentication being used for onsite and a number of cloud services using Single Sign on (SSO) systems, it is very important that the system be robust and ensure that the authentication is valid.
At the heart of the process is the password. Explain the importance of the function of the password in user authentication. Also explain why an administrator should have two accounts, one for day to day activities and one for tasks that require elevated privileges.
Research current best practices for Windows credentials including length and complexity requirements and state what the current best practices are for setting passwords in a Windows Domain. Explain whether these change if being used as a SSO for cloud services.
Use and cite relevant information from your research. You should have at least two (2) authoritative sources.
Task 2: Apply a common security solution (20%)
With Single Sign-on tools domain passwords are used both onsite and in the cloud, requiring that they be suitably complex. You are provided with a Domain Controller and member server in the Yoobee Sandbox on ACI Learning Skill Labs. Using these virtual machines complete this task.
Configure password complexity
- Using current best practices as stated in Task 1 define the settings for the domain password policy covering:
a. Complexity
b. Length
c. Maximum duration
d. Minimum duration - On PLABDC01 configure the default GPO used for defining password settings (screenshot each configuration)
- Create two (2) user accounts for yourself in AD DS. For the first one use your name only. For the second, add “-admin” to the username. Add this account to the domain admins security group. Screenshot the creation of each new account and the group memberships.
- Log onto workstation – try to set a password that does not meet complexity rules and screenshot the error message. Explain why it was not accepted.
- Set a valid password – screenshot the notice that the password has been changed.
Task 3: Research available technologies to enhance authentication using emerging technologies (30%)
Research emerging technologies which are currently available or under development that will enhance user authentication beyond tradition password based methods. The technologies must be suitable for ABC Print Services. How do they compare in terms of security, usability, and scalability?
The Technologies may include:
- Fine Grained Password Policies
- Multi-Factor Authentication (MFA)
- Passwordless authentication (e.g. passkeys, biometrics, hardware tokens)
- Conditional access policies
- Cloud IAM (Identity and Access management) technologies
Some of the issues with password-based authentication include not being able to remember passwords because a random collection of numbers, letters and symbols or sequencing passwords where a number is incremented. What are the risks associated with the emerging technologies.?
As this is a research question, you are expected to cite at least three reliable sources for information gathered.
Task 4: Provide recommendation for security solution (20%)
The following questions relate to ABC Print Services. You must ensure that your discussion centres on solutions relevant to ABC Print Services.
Based on the technologies research in Task 3, provide a recommendation to ABC Print Services on how the authentication processes could be enhanced. Clearly describe the proposed solutions including the type of technologies (i.e. whether MFA, Passwordless, Cloud IAM, or conditional access, or other types).
Your recommendation must be tailored for the who of ABC Print Services at both the Hamilton and Taupō offices. Your response must include:
- The benefit to remote access and mobile staff
- How cloud services would be integrated with on-premise infrastructure
- Risks associated with the technologies, particularly should a component such as Internet access or VPN fail.
Explain why this technology is appropriate for ABC Print Services by evaluating:
- Security: How does it mitigate current risks
- Usability: Will it be accessible to all staff members who may have sight, motion, or language challenges?
- Scalability: Is there any form of cap on the number of people who can effectively use this technology?
Student Guide
Whenever explain is requested looking for ”SEE” (State, elaborate, example) and whenever ”Create” or ”modify” is requested looking for screenshots where values are entered and an explanation about the value being entered.
Task 1
Authoritative sources are considered to be ones that are created by a reliable source such as the creator or publisher of the product or by a source which has considerable experience and expertise in the area. The sites must be configured to prevent updates from other unauthorised sources.
Task 2
If unsure how to access your ACI Learning labs, please contact your tutor. If you desire to create your own domain, this is acceptable.
Please remember that ACI labs have a time limit of 90 minutes. Ensure that you get the screenshots.
An option would be to video using the Game Bar (Windows + Alt+ r on a Microsoft Windows device). Password policies applied to the provided virtual machines will continue until the devices are reset or new policies defined.
Ensure that you get a screenshot of an attempt to change the password to an invalid password being rejected and to a valid password being accepted.
Task 3
See notes for Task 1 re what is an authoritative website. A reminder that because Wikipedia is collaborative and anyone can update on any topic it is not considered an authoritative website.
A recommendation is to have an introduction stating what trying to do in the report, a body where explain the issues and how they are being addressed, and a conclusion.
This section is an exploration of the technologies. It is recommended that provide recommended scenarios where the solutions would be most appropriate. A table with
| Technology | Description | Strengths | Weaknesses |
Might help make clear to the assessor your analysis. Don’t forget that are asked to compare them for suitability in terms of
- Security,
- Usability, and –
Task 4
In task 4 you are requested to make a recommendation based on your analysis in Task 3. With Task 4
you have to remember the size and type of company ABC Print Services is. The recommendations must be appropriate for a company that uses onsite, and cloud services distributed over at least two locations. It is not a large company, but it does handle sensitive data for clients, so they have to be confident in the confidentiality of the documents being printed. This confidentiality is highly dependant upon the authentication process in or to manage access to sensitive information.
Report Writing
This submission involves writing a report. 10% of the grade for the assessment is based on the report writing. This involves the use of headings, clear structure, spelling and grammar, as well as citations.
It is recommended that start with the titles and then the key ideas under each title. Once have the key ideas expand each paragraph to explain the ideas.
Make sure that the proofing language is set to “English (New Zealand)”. Two major spelling differences between American English and New Zealand English are:
- Verbs that end in “-ize” in American English are spelled with “-ise” in New Zealand English — for example, summarize becomes summarise.
- Nouns ending in “-ization” are spelled “-isation” — for example, organization becomes organisation.
Setting the proofing language correctly will help ensure that these and other regional spelling conventions are applied consistently.
The final point is to ensure that cite and reference properly. Word has a built-in citation and referencing tool. It is under References. If select “Insert Citation” it will ask if citing an existing reference or new one. If new add the details and will automatically create the citation. The references are carried over so only need to enter the details once. If that same source is used in future reports, it is available to be used again.
Marking Rubric
| Task | Weighting | A | B | C | D | E |
| Task 1 | 20% | Demonstrates a thorough understanding of the importance of
authentication in Windows Domain or SSO environments, including why an administrator should have a separate authentication for tasks that require elevated privileges. Has researched, presented, and accurately explained best practices for password length and complexity using credible sources.
(20 Marks) |
Shows a good understanding of the importance of passwords in the securing of Windows Domains and SSO. Has researched and presented a mostly accurate explanation of current best practices.
(15 Marks) |
Demonstrates a basic understanding of the role of passwords in security within the context of Windows Domain or SSO. The research is limited and the recommendations on the best practices are dated or lack clarity.
(10 Marks) |
The explanation of the role of passwords in securing a Windows Domain or SSO is limited to a few statements without explanation and the best practices lack accuracy.
(8 Marks) |
The explanation or the role of passwords is missing
or
Identifying best practices is missing.
(0 Marks) |
| Task 2 | 20% | Has correctly applied all the best practices
for complexity, length, minimum and maximum duration as stated in Task1 with screenshots for each configuration and demonstrated it being applied when trying to set passwords.
(20 Marks) |
Screenshots show has applying most of the best practices as stated in Tasks 1 correctly. Has demonstrated that the policies are being applied when set the passwords in member server.
(15 Marks) |
Has demonstrated, using screenshots, correctly setting password settings, but not as per best practices or have not demonstrated the updated password rules being applied.
(10 Marks) |
Password settings are not according to best practices or have not set critical (password length or complexity) rules or configured ins such a way that rules will not be applied or have have not demonstrated the rules being applied.
(8 Marks) |
No evidence of passwords settings
being applied or tested
(0 Marks) |
| Task 3 | 30% | Demonstrates a well researched and insightful analysis using at least three sources of at least three (3) emerging technologies. Each is clearly explained with examples and evaluated security, scalability, and usability. The risks are thoughtfully identified.
(30 Marks) |
Describes and evaluates at least 3 relevant technologies with good detail. Comparison across security, usability, and scalability is mostly clear. Risks are identified with 2–3 reliable sources cited.
(22.5 Marks) |
Covers 2–3 technologies with basic evaluation. Some comparison is made, but may lack depth or clarity. Risks are mentioned but not well developed. At least 2 sources are cited.
(15 Marks) |
Describes 1–2 technologies with limited evaluation. Comparison is vague or incomplete. Risks are minimally addressed. Only 1 source cited or sources lack credibility.
(12 Marks) |
Technologies are poorly described or irrelevant. No meaningful comparison or risk analysis. No sources cited or sources are unreliable. (0 Marks) |
| Task 4 | 20% | Provides a welljustified, tailored
recommendation using appropriate technologies (e.g., MFA, Passwordless, Cloud IAM). Clearly addresses remote access, cloud integration, and risks. Evaluates security, usability (including accessibility), and scalability with strong relevance to both Hamilton and Taupō offices. (20 Marks) |
Recommendation is mostly relevant and justified. Covers key areas with minor gaps in detail or clarity. Technologies are appropriate and evaluation is generally sound.
(15 Marks) |
Provides a basic recommendation with some relevance. Covers most required areas but lacks depth or clear evaluation. Technologies may be generic.
(10 Marks) |
Recommendation is vague or partially relevant. Limited coverage of required areas. Evaluation is superficial or incomplete. (8 Marks) | Recommendation is unclear, inappropriate, or not tailored to ABC Print Services. Key areas are missing or misunderstood.
(0 Marks) |
| Report
Writing |
10% | The report is well structured with introduction, body and conclusion. The
headings are clear. The format is as prescribed. Has been spell check for New Zealand spelling and culturally appropriate. Referencing is APA 7. (10 Marks) |
The report has the appropriate structure and headings. Has been formatted well
but contains a few spelling errors (for New Zealand) and is culturally appropriated. Referencing is APA 7 but has some errors. (7.5 Marks) |
The report is acceptable as a report. Does not have an introduction or
conclusion. The headings are present, but the referencing is not APA 7. (5 Marks) |
Report does not have a report structure
OR No reference list. (4 Marks) |
Invalid format, no citations, poor spelling,
(0 Marks) |
🔹 Need Help With CIT504 Introduction to Information Technology Assessment?
Hire NZ Native Experts 24/7.
Many students find the CIT504 Introduction to Information Technology assessment challenging due to security concepts, research requirements, and limited time for lab-based tasks. Instead of stressing, learners now choose guidance from trusted academic experts. NZ Assignment Help provides Information Technology assignment help aligned with YOOBEE assessment standards, including case study analysis and APA 7 referencing. You can also explore our expert-written assignment samples to check content quality. Get started today with yoobee college assignment helper and receive a custom, human-written, plagiarism-free CIT504 solution.
- EDU725 Inclusive Early Childhood Education Assessment 2, 2026 | Open Polytechnic
- 110733 Financial Accounting and Reporting Assessment 1, 2026 | Massey University
- BSNS5004 Change and Innovation Assessment 3 2026 | Open Polytechnic
- BSNS4601 Introduction to Project Management Assessment 1, 2026 | Open Polytechnic
- 218.763 Advanced Construction Law Assignment 1 2026 | Massey University
- BUSS611 Organisational Decision-Making Skills Assignment 1 2026 | AIS
- FSC522 The Regulatory Framework Assessment 2 2026 | Open Polytechnic NZ
- BUSS508 Economics and International Business Assessment 1 2026 | AUT
- BSRV4603 Real Estate Sales and Marketing Assessment 1 2026 | Open Polytechnic
- STATS 330 Statistical Modelling Assignment Question | University of Auckland


